Unmasking the Unseen: How Machine Learning Uncovers Zero-Day Vulnerabilities
In today's digital landscape, cybersecurity threats are constantly evolving, and one of the most concerning challenges for organizations is dealing with zero-day vulnerabilities. Zero-day vulnerabilities are software weaknesses exploited by cybercriminals before the software developer becomes aware of them, leaving no time for traditional security patches. Detecting and mitigating these vulnerabilities is crucial for safeguarding sensitive data and maintaining the integrity of systems. This is where machine learning plays a pivotal role.
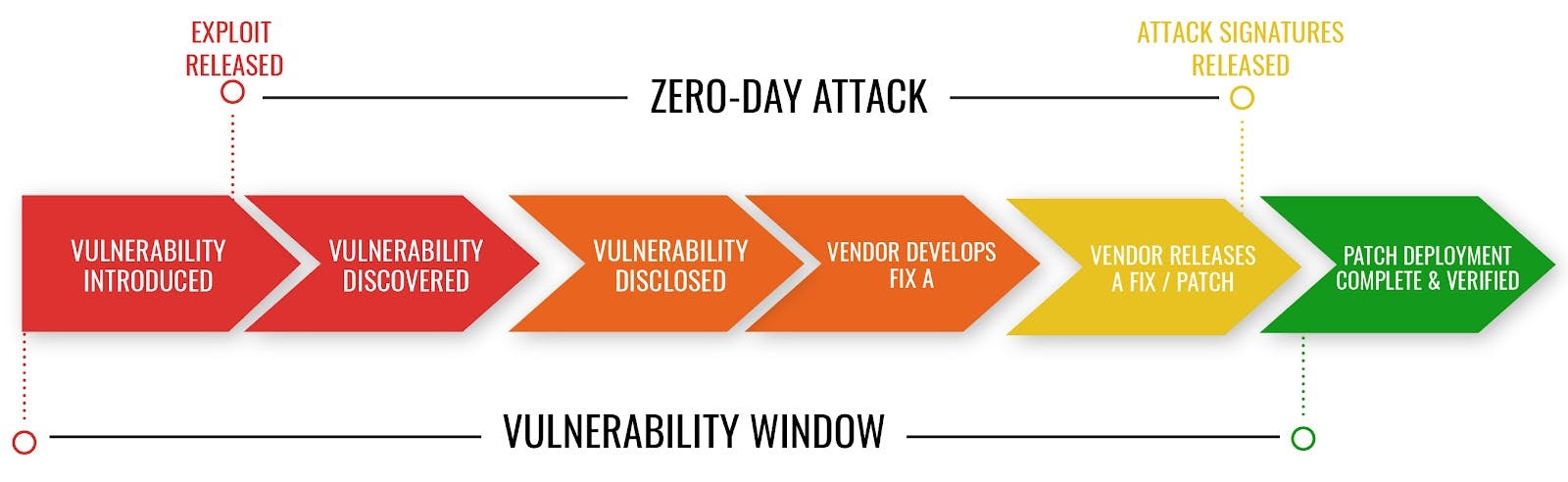
Zero-day vulnerabilities are called "zero-day" because organizations have zero days to prepare for them. Cybercriminals exploit these vulnerabilities immediately after discovery, making them incredibly difficult to defend against. These exploits can lead to data breaches, system compromise, and financial losses.
Zero-Day Vulnerability Response Steps
The discovery and handling of zero-day vulnerabilities involve several steps, from identification to mitigation. Here is a general procedure for dealing with zero-day vulnerabilities:
Identification:
Suspicious Activity Monitoring: Continuously monitor network and system activities for unusual behavior, patterns, or anomalies.
Threat Intelligence Feeds: Subscribe to threat intelligence services and feeds to stay updated on emerging threats and vulnerabilities.
Security Research: Engage with security researchers and organizations that specialize in vulnerability discovery.
Detection:
Intrusion Detection Systems (IDS): Utilize IDS tools to detect suspicious network traffic or system activity that might indicate a zero-day exploit.
Behavioral Analysis: Implement machine learning models or behavioral analysis techniques to identify deviations from normal system behavior.
Endpoint Detection and Response (EDR): EDR solutions can help detect and respond to unusual behavior on endpoints and provide valuable insights.
Validation:
Once a potential zero-day vulnerability is detected, security teams should validate the finding to ensure it's not a false positive.
Analyze the nature and extent of the vulnerability to determine its severity.
Reporting:
Report the zero-day vulnerability to the relevant vendor or organization responsible for the affected software or system. Follow responsible disclosure practices.
Share the vulnerability details with cybersecurity organizations and communities to alert others and coordinate response efforts.
Temporary Mitigation:
Until a vendor patch or fix is available, implement temporary mitigation measures, such as disabling certain features or restricting access to vulnerable components.
Consider isolating affected systems from the network to prevent further exploitation.
Vendor Communication:
Maintain open communication with the vendor or developer responsible for the affected software.
Collaborate with the vendor to develop and test a security patch or update to address the zero-day vulnerability.
Patch Deployment:
Once a patch or update is available, apply it to all affected systems promptly.
Ensure that patch management practices are in place to keep systems up to date with the latest security fixes.
Post-Incident Analysis:
After mitigating the zero-day vulnerability, conduct a thorough post-incident analysis to understand how the vulnerability was exploited, its impact, and any lessons learned.
Use this analysis to improve cybersecurity practices and incident response procedures.
Monitoring and Vigilance:
Continue monitoring for any signs of further exploitation or variations of the zero-day vulnerability.
Stay vigilant by keeping up with threat intelligence and security research.
Regular Updates:
- Regularly update and review your organization's security policies, procedures, and technologies to adapt to evolving threats.
Zero-day vulnerabilities pose significant risks, and their discovery and handling require a coordinated and proactive approach. Collaboration with the security community, vendors, and timely patch management are essential elements in effectively addressing these vulnerabilities.
Traditional Approaches vs. Machine Learning
Traditionally, organizations relied on signature-based antivirus software and intrusion detection systems to protect against known threats. However, these methods are inadequate when it comes to zero-day vulnerabilities. Machine learning offers a more proactive and practical approach
Anomaly Detection: Machine learning models can be trained to understand the baseline behavior of software and networks. When deviations from this baseline are detected, it raises an alert, potentially signaling a zero-day exploit.
Pattern Recognition: ML algorithms can recognize patterns and anomalies humans might overlook. They can analyze vast amounts of data quickly, identifying irregularities that could indicate an attack.
Predictive Analysis: By analyzing historical data, machine learning models can predict potential zero-day vulnerabilities based on trends and commonalities in past exploits.
Machine Learning Models for Zero-Day Vulnerability Detection
Machine learning models can be employed to detect zero-day vulnerabilities by analyzing various aspects of software and network behavior. Here are some commonly used techniques:
Behavioral Analysis: Machine learning models can learn the normal behavior of software applications, including system calls, network traffic patterns, and user interactions. Any deviation from this learned behavior can trigger an alert.
Feature Engineering: Features such as file signatures, network packet headers, and code execution sequences can be extracted and fed into machine learning algorithms. These features help models identify patterns associated with zero-day exploits.
Deep Learning: Neural networks, particularly convolutional neural networks (CNNs) and recurrent neural networks (RNNs), can be applied to analyze complex data, making them valuable for detecting subtle anomalies that might signal a zero-day attack.
Natural Language Processing (NLP): NLP techniques can be used to analyze text data, such as security logs and vulnerability reports, to identify language patterns indicative of zero-day vulnerabilities.
Data Sources for Training Models
The effectiveness of machine learning models for zero-day vulnerability detection relies heavily on the quality and diversity of the data used for training. Here are some essential data sources:
Security Logs: Logs generated by firewalls, intrusion detection systems, and antivirus solutions provide valuable insights into network and system activities.
Vulnerability Databases: Historical data on known vulnerabilities can help identify common patterns that may indicate zero-day vulnerabilities.
Dark Web Monitoring: Monitoring underground forums and hacker communities can provide early indicators of new exploits and vulnerabilities.
Honeypots: Deploying honeypots in a network can attract attackers and capture their activities, helping to train machine learning models.
The High Stakes of Zero-Day Vulnerabilities
Zero-day vulnerabilities are like hidden landmines in the digital landscape. They can be exploited by cybercriminals for various malicious purposes, including:
Data Breaches: Zero-day exploits can lead to unauthorized access to sensitive data, such as personal information, financial records, or proprietary business data.
Malware Distribution: Cybercriminals often use zero-day to deliver malware, including ransomware and spyware, which can have devastating consequences for individuals and organizations.
System Compromise: Exploiting a zero-day vulnerability can grant attackers control over a victim's system, allowing them to carry out further attacks or use the compromised machine as a part of a larger botnet.
Espionage: Nation-states and threat actors may use zero-day vulnerabilities for espionage, targeting governments, corporations, or other high-value entities to steal sensitive information or conduct cyber espionage.
Financial Loss: The fallout from a successful zero-day attack can result in significant financial losses, including the cost of incident response, legal fees, and damage to an organization's reputation.
Challenges and Considerations
While machine learning is a powerful tool for zero-day vulnerability detection, it's not without its challenges
False Positives: ML models may generate false positives, which can lead to alert fatigue among security teams. Fine-tuning models and improving data quality can help mitigate this issue.
Data Privacy: Handling sensitive data for training ML models raises privacy concerns. Organizations must implement robust data protection measures.
Adversarial Attacks: Cybercriminals can attempt to manipulate ML models to evade detection. Constant monitoring and model updates are essential to counter this threat.
The Role of Threat Intelligence
Integrating threat intelligence into machine learning models can significantly enhance their ability to detect zero-day vulnerabilities. Threat intelligence feeds provide up-to-date information on emerging threats and vulnerabilities. Machine learning models can use this data to stay current and adapt to the evolving threat landscape.
Human-Machine Collaboration
While machine learning is a powerful tool for zero-day vulnerability detection, it's not a replacement for human expertise. Security analysts play a crucial role in interpreting alerts generated by ML models, investigating potential threats, and making informed decisions about remediation.
Ongoing Monitoring and Adaptation
The cybersecurity landscape is dynamic, with new attack techniques constantly emerging. Organizations must continuously monitor and update their machine-learning models to remain effective against zero-day threats. Regular model retraining and fine-tuning are essential to keep pace with evolving attack methods.
Conclusion
Zero-day vulnerabilities pose a significant challenge to cybersecurity, but machine learning offers a promising solution for their detection. By leveraging machine learning models, organizations can enhance their ability to identify zero-day exploits early, reducing the risk of data breaches and system compromises. However, successful implementation requires a comprehensive strategy that includes high-quality data, ongoing monitoring, and collaboration between humans and machines. In the ever-evolving world of cybersecurity, the combination of machine learning and human expertise is a potent defense against zero-day threats.
